HOW MANY TIMES WAS A USB STORAGE DEVICE CONNECTED TO A COMPUTER?
The Windows operating system stores valuable information about connected Universal Serial Bus (USB) storage devices in the Windows Event Logs which are located in the following file path.
{Drive}:\Windows\System32\winevt\Logs\
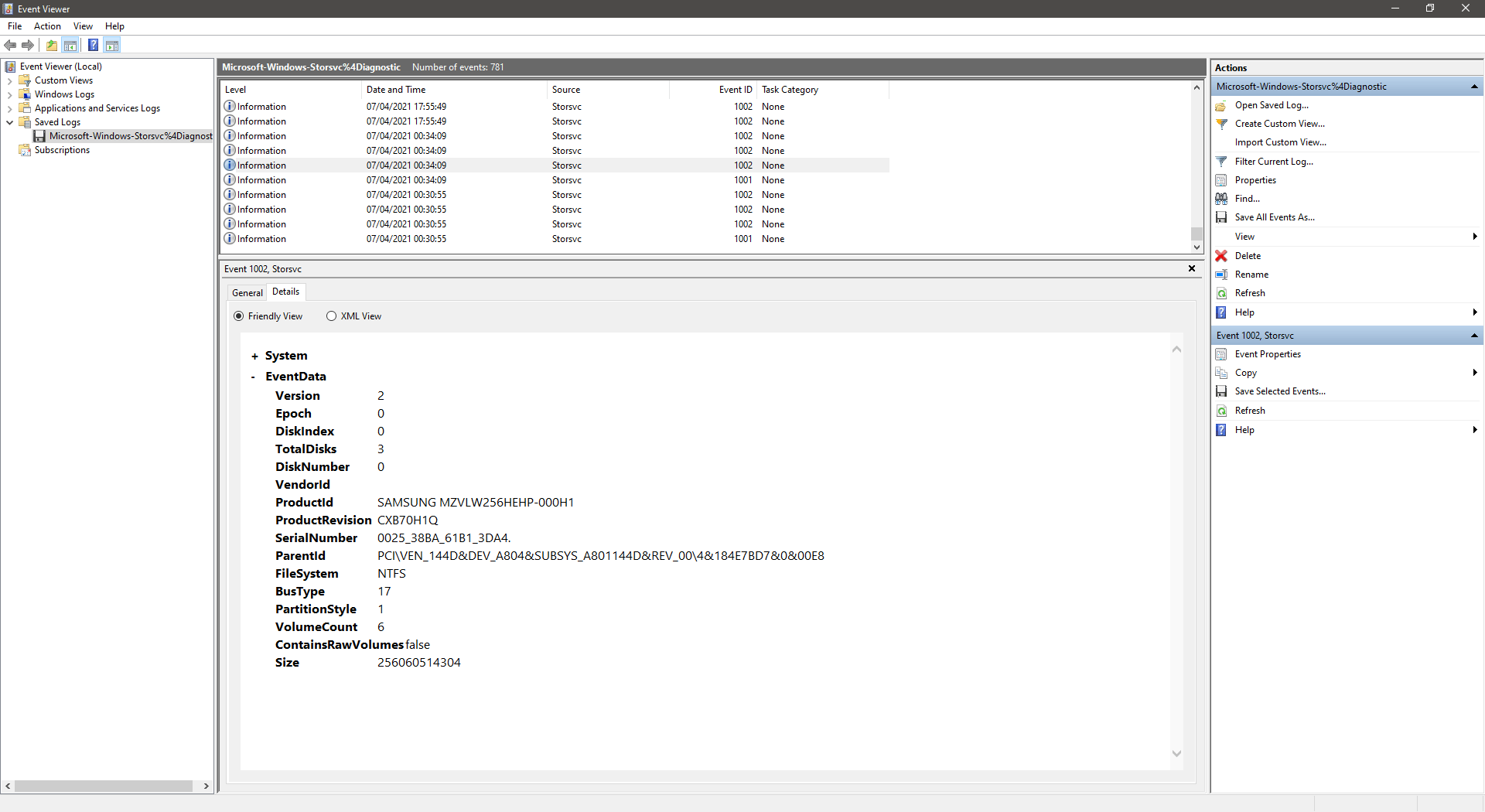
To find the number of times that a specific USB storage device has been connected to a suspect computer, review the information available in Microsoft-Windows-Storsvc%4Diagnostic.evtx. It is a significant event log file that contains vital information about connected USB storage devices. The Event IDs 1001 and 1002 contain System related information such as the Timestamp, Device Name and User Identifier, and Event related data such as the Serial Number and Product Identifier which can be used for identifying the specific storage device.
KNOWN SERIAL NUMBER
If you know the serial number of the USB storage device, you can search through the Event Log and make a note of each interaction that the device has had with the suspect computer. Key details that should be noted consist of SystemTime and the number of events that have been logged. Pay attention to the timestamp information as it is presented in the Coordinated Universal Time (UTC) format.
UNKNOWN SERIAL NUMBER
There may be situations where you do not know the serial number of the USB storage device that you are attempting to find. You can try to narrow down the list of possible devices, if you know the vendor or brand name of the USB storage device. The event log contains the ProductID and VendorID entries which may be of assistance. If even this information is unknown to you, the FileSystem entry may be of help, provided that you know what file system the target device is using.
SYSTEM
Provider
[Name] _____________ Microsoft-Windows-Storsvc
[Guid] _____________ {a963a23c-0058-521d-71ec-a1cce6173f21}
EventID _____________ 1001
Version _____________ 0
Level _______________ 4
Task ________________ 0
Opcode ______________ 0
Keywords ____________ 0x8000000000000000
TimeCreated
[SystemTime] _______ 2022-04-14T16:34:52.1567835Z
EventRecordID _______ 480
Correlation
[ActivityID] ______ {8e494d8d-16da-0004-d755-498eda16d801}
Execution
[ProcessID] _______ 14980
[ThreadID] ________ 24180
Channel _____________ Microsoft-Windows-Storsvc/Diagnostic
Computer ____________ LAPTOP-6P571J62
Security
[UserID] __________ S-1-5-18
EVENTDATA
Version _____________ 2
DiskNumber __________ 2
VendorId ____________ WD
ProductId ___________ Elements SE 2623
ProductRevision _____ 1026
SerialNumber ________ WXE2A51CSLHZ
ParentId ____________ USB\VID_1058&PID_2623\5758453241353143534C485A
FileSystem __________ exFAT
BusType _____________ 7
PartitionStyle ______ 0
VolumeCount _________ 1
ContainsRawVolumes __ false
Size ________________ 1000170586112
Above are the entries contained in Microsoft-Windows-Storsvc%4Diagnostic.evtx.
HUNGRY FOR MORE?
Cyber Security Misconceptions
Do you lack the educational background and coding skills required to land a job in the cyber security industry? Several misconceptions exist regarding what it takes to break in! Find out more why you could and should pursue a career in cyber security.
Malware Analysis with ChatGPT
CHATGPT POWERED MALWARE ANALYSISDuring late 2022 and early 2023, ChatGPT made headlines in the tech industry and everyone caught scent of the excitement! ChatGPT is a truly intriguing example of the capabilities of Artificial Intelligence, and how it can be used in...
Triage
What is Triage in the context of Cyber Security, and why is it a crucial step in Security Operations and Incident Response? Find out more!
Endpoint Isolation – The Ultimate Remediation Action
Learn about endpoint isolation and discover how it can stop malware from spreading and prevent data exfiltration. You will also learn about its limitations and consequences for business operations.
Is coding required for Cyber Security?
Are you aspiring to work in the Cyber Security industry but lack coding skills? Is it really a must-have skill to possess in order to succeed? Find out the answer!
Do I need a college degree for Cyber Security?
Have you ever been told that you cannot get into the cyber security field without a college or university degree? If you have, you are not alone! Self-learning is a perfectly viable alternative!
IACIS Windows Forensic Examiner review
The International Association of Computer Investigative Specialists (IACIS) offers an affordable and comprehensive training solution to address the need for training in Windows Forensics.
Unable to Boot into Linux? Try this!
You have just installed a Linux distribution on your computer and now your system refuses to boot. The option you may have overlooked is Trusted Execution Technology.
What does a Cyber Security Analyst do?
The role of a Cyber Security Analyst is one of great importance and responsibility. While the work can be highly rewarding, it also requires great deal of patience.
SANS SEC504 / GCIH – Best foundational cyber security certification!
SANS SEC504 is a six-day course that lays a solid foundation of the core principles of cyber security upon which you can build your cyber security career.